This challenge is all about cracking hashes and figuring out what’s hidden inside. It’s perfect for beginners looking to get their hands dirty with hash identification and cracking techniques. There’s no one “right” way to tackle it, but this is how I went about it.
First Steps: Decoding the Hashes
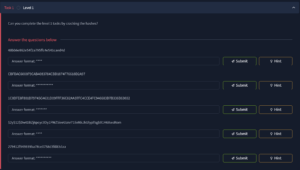
At first glance, we’re greeted by what seems like a jumble of random letters and numbers. It’s clear these are hashes that we need to crack.
A simple and effective way to start is by using CrackStation.net. Most of these hashes can be directly pasted there, and the site will do the heavy lifting, decoding them for us.
It’s a quick win, but let’s keep going!

We can see that CrackStation helps us crack almost all the hashes in the first section, but there’s one that doesn’t work—specifically, the 4th question. For this one, we’ll need to use hashcat with the rockyou.txt wordlist.
Now, we could take the time to run through the entire list, but given the hint that the answer is only 4 letters, we can save time by filtering rockyou.txt to include only 4-letter words. To make this easier, I wrote a Bash script to handle the filtering:
#!/bin/bash
# Prompt the user for input
read -p “Enter the desired word length: ” number
read -p “Enter the path to the .txt file: ” file
# Validate inputs
if [[ ! -f “$file” ]]; then
echo “Error: File not found!”
exit 1
fi
if ! [[ “$number” =~ ^[0-9]+$ ]]; then
echo “Error: Please enter a valid number!”
exit 1
fi
# Generate output filename
output_file=”${file%.txt}_short.txt”
# Filter and save words with the specified length
grep -oE “\b[[:alnum:]]{$number}\b” “$file” > “$output_file”
# Confirm completion
echo “Filtered words saved to $output_file”
Here’s how it works:
- The script asks for the number of letters (in our case, 4) and the path to the wordlist (
rockyou.txt). - It checks if the file exists to prevent errors.
- It filters the wordlist to keep only the words matching the specified length using
grep. - The filtered list is saved as
<original_name>_short.txt.
This script along with others I’ve written can be found on my GitHub. (Soon to be post here as well!)
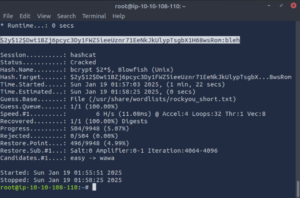
With this script, we can quickly narrow down rockyou.txt to just the 4-letter words, making our hashcat process much faster. After running the script, point hashcat to the new filtered list and let it do the rest!
hashcat -a 0 -m 3200 hash.txt /usr/share/wordlists/rockyou_short.txt –force
for this command to work you need to put the hash you want to crack into a file named hash.txt
On To Level 2
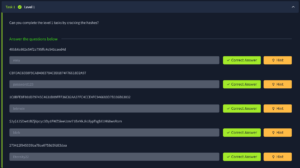
This one look a little more interesting. Lets see what we can find!
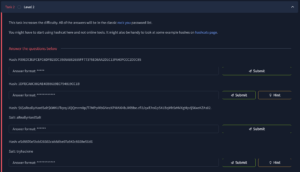
Again CrackStation gives us the easy answers for the first two. The next ones however we notice the word Salt:
Looks Like we need hashcat again. Lets’ start by making a new list with 6 letters since we got that clue from the question.
Once we have our shortened list and the hash in our hash.txt file we can run hashcat against it.
(This might take some time so relax.)
hashcat -m 1800 -a 0 hash.txt rockyou_short.txt
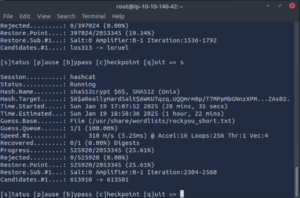
As we can see Hashcat is going to take some time to run even with our shortened word list.
You are welcome to try any other wordlist you like. The shortening script will work with any .txt file.
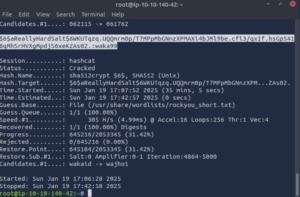
That answers one of our last questions. Let’s figure out the last one now.
We know with the hints provided that we have 12 characters and the actual hint says “HMAC-SHA1”.
Working with that in mind we can figure this one out pretty quick.